NIST: National Institute of Standards and Technology
The National Institute of Standards and Technology (more information) is a federal agency of the USA based in Maryland. NIST is primarily responsible in the area of IT security and, in addition to new encryption methods, also develops processes and technologies for securely deleting data carriers that are used in all areas worldwide. Since version 5.80, the toolstar®shredderLX supports the two standards NIST Purge and NIST Clear.

NIST Purge und NIST Clear
NIST Purge and NIST Clear are the two standards published by NIST for erasing all types of data storage media (HDD, SSD, NVMe, USB, etc.). NIST Purge is the more secure standard of the two. However, a hard drive must support certain hardware properties in order for NIST Purge to run. This includes, for example, the ATA SANITIZE and NVM FORMAT_NVM Command Set. NIST Clear uses a combination of ATA SECURE_ERASE_UNIT and classic disk overwrite. toolhouse's recommendation is to configure the two standards in dependency in the program , so that NIST Purge is always attempted and if this standard is not possible NIST Clear is applied. NIST Clear is supported on all media, regardless of the hardware characteristics of the media. This gives you a 100% fallback if NIST Purge is not supported.
ATA SECURE_ERASE_UNIT, ATA SANITIZE and NVM FORMAT_NVM
ATA SECURE_ERASE_UNIT, ATA SANITIZE and NVM FORMAT_NVM are special extensions of the ATA or NVM command set for erasing data carriers. Each specification has its own sub-points. This results in the following list of possibilities. A disk supports either none or several of the following:
- Secure Erase
- Enhanced Secure Erase
- Sanitize Overwrite
- Sanitize Block Erase
- Sanitize Crypto Scramble
- NVM Format User Data Erase
- NVM Format Cryptographic Erase
NIST Purge and NIST Clear, depending on support, perform one of these functions to completely wipe the hard drive. The hard drive uses an internal procedure (SSD and NVMe) to delete all NAND blocks and, under certain circumstances, also reset them to their FOB (fresh-out-of-box) state. Afterwards, an SSD storage medium is as fast as when it was initially used and can continue to be used without any concerns.
Additional security is provided, among other things, by the fact that NAND blocks or sectors that have been swapped out by the firmware are deleted and overwritten. In addition, once the deletion process has been started, it can no longer be aborted. The disk will continue to perform the deletion until it is completely completed. Even unplugging the power cannot stop the process. The disk will not function properly again until the erasure process has been completed.
The two methods NIST Purge and NIST Clear contain, among other things, additional security functions for checking the deletion. A special verification process is used for this. This ensures that the data has really been deleted. All operations described above are carried out for you fully automatically by toolstar®shredderLX and then in certificates and protocols documented.
Activation / use in the toolstar®shredderLX program
To use the NIST Purge and NIST Clear methods in the toolstar To be able to use ®shredderLX, only minimal configuration effort is required.
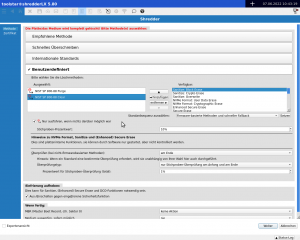
- Open the Shredder Manual item on the home page
- Select the hard drives to be deleted (in the standard version up to 4 at the same time)
- Go to “Custom”
- In the list of dependencies, set the following
- Press Next and the process will start automatically
Information on creating secure deletion processes
- Always make sure to include a fallback in your scripts to ensure that everything is always deleted. This means that lastly you select, for example, a classic override or NIST Clear.
- Make sure to connect the data storage devices to their native port (ATA, SCSI, USB, PCI, etc.) if possible. Only then can you be 100% sure that all commands are correctly transmitted to the data carrier. This also increases the speed of deletion immensely.
- Always select the item “Turn off and on against frozen security functions”. This step is required to enable Enhanced Secure Erase, Secure Erase and the resolution/detection of a DCO and HPA.
- Always let the program create a deletion certificate and a deletion log. The deletion certificate is your and your customer's proof of successful deletion of the data medium. The deletion log contains all important information about the deletion process and, in the event of an error, also detailed information about the cause of the problem.
- Always try a combination of a firmware-based standard and classic hard drive overwriting. Or use NIST Purge and NIST Clear for an automated combination. Classic overwriting is required to stay within an international standard. NIST Purge and NIST Clear are such a combination and at the same time also an international standard.
- Always clarify with the customer what type of data is on the media in order to use the correct method. Customers such as federal authorities may also specify a process or standard to use.